Date: 17/12/2022
Relevance: GS-3: Science and Technology- Developments and their Applications and Effects in Everyday Life; Role of Media and Social Networking Sites in Internal Security Challenges, Basics of Cyber Security.
Key Phrases: End-to-End Encryption, Online interactions, Metadata, Public Key Cryptography, Compromised Endpoints, Digital Platforms, Tamper-proof, Safety tools and Features, Societal Reliability of the Internet, Data Privacy.
Context:
- Recently, Apple announced it will be increasing the number of data points protected by end-to-end encryption on iCloud from 14 to 23 categories.
Key Highlights:
- Similarly, Elon Musk, in November, said that he wanted Twitter DMs to be encrypted.
- However, government agencies are not happy with the development
because of the threat that end-to-end encryption and user-only access pose.
- End to end encryption hinders government agency’s ability to protect people from cyber-attacks, violence against children, and terrorism.
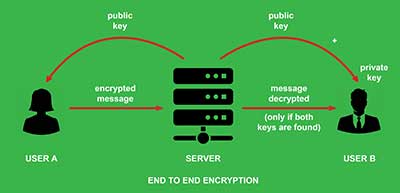
What is End-to-End Encryption?
- End-to-end encryption is a method of secure communication that prevents third parties from accessing data while it's transferred from one end system or device to another.
- It prevents third parties like cloud service providers, internet service providers (ISPs) and cybercriminals from accessing data while it is being transferred.
- The process of end-to-end encryption uses an algorithm that
transforms standard text into an unreadable format.
- This format can only be unscrambled and read by those with the decryption keys, which are only stored on endpoints and not with any third parties including companies providing the service.
Where is it used?
- End-to-end encryption is used to secure communications.
- Many popular messaging service providers use end-to-end encryption, including Facebook, WhatsApp and Zoom.
- End-to-end encryption has long been used when transferring business documents, financial details, legal proceedings, and personal conversations.
- End-to-end encryption is used when data security is necessary, including in the finance, healthcare and communications industries.
- It is often used to help companies comply with data privacy and security regulations and laws.
- It is also used to secure passwords, protect stored data and safeguard data on cloud storage.
What does End-to-End Encryption protect against?
- Prying eyes
- It keeps anyone other than the sender and intended recipient from reading message information in transit because only the sender and recipient have the keys to decrypt the message.
- Tampering
- It also protects against tampering with encrypted messages.
- There is no way to predictably alter a message encrypted this way, so any attempts at altering would be obvious.
What doesn't End-to-End Encryption protect Against?
- Metadata
- While end-to-end encryption protects the information inside a message, it does not conceal information about the message, such as the date and time it was sent or the participants in the exchange.
- Compromised Endpoints
- If either endpoint has been compromised, an attacker may be able to see a message before it is encrypted or after it is decrypted.
- Attackers could also retrieve keys from compromised endpoints and execute a man-in-the-middle attack with a stolen public key.
- Vulnerable Intermediaries
- Sometimes, providers claim to offer end-to-end encryption when what they really offer is closer to encryption in transit.
- The data may be stored on an intermediary server where it can be accessed.
Why are Tech Companies using it?
- The extra layer of protection would be valuable to targets of hacking attacks launched by well-funded groups.
- The focus on end-to-end encryption seems to stem from the company’s desire to position itself as a provider of secure data storage and transfer services.
- End-to-end encryption is also seen as a technology that secures users’ data from snooping by government agencies, making it a sought-after feature by activists, journalists, and political opponents.
Advantages:
- Security in transit
- End-to-end encryption uses public key cryptography, which stores private keys on the endpoint devices.
- Messages can only be decrypted using these keys, so only people with access to the endpoint devices are able to read the message.
- Tamper-proof
- With end-to-end encryption, the decryption key does not have to be transmitted because the recipient will already have it.
- If a message encrypted with a public key gets altered or tampered with in transit, the recipient will not be able to decrypt it, so the tampered contents will not be viewable.
- Compliance
- Many industries are bound by regulatory compliance laws that require encryption-level data security.
- End-to-end encryption can help organizations protect that data by making it unreadable.
Disadvantages:
- Complexity in defining the endpoints
- Some end-to-end encryption implementations allow the encrypted data to be decrypted and re-encrypted at certain points during transmission.
- This makes it important to clearly define and distinguish the endpoints of the communication circuit.
- Too much privacy
- Government and law enforcement agencies express concern that end-to-end encryption can protect people sharing illicit content because service providers are unable to provide law enforcement with access to the content.
- Visible Metadata
- Although messages in transit are encrypted and impossible to read, information about the message - date sent and recipient, for instance - is still visible, which may provide useful information to an interloper.
- Endpoint Security
- If endpoints are compromised, encrypted data may be revealed.
Conclusion:
- While cryptographers and cybersecurity experts argue that attempts by law enforcement to weaken encryption with backdoors are ill-advised and could compromise the reliability of the internet, the move by tech companies to use end-to-end encryption to secure more user data seems to be getting stronger.
Source: The Hindu
Mains Question:
Q. What is End-to-End Encryption? Also, mention the associated advantages and disadvantages of using it. (250 Words)