Social Engineering Attacks
Social engineering is the term used for an extensive range of malicious activities achieved through human interactions. It uses psychological manipulation to dodge users into making security mistakes or giving away sensitive information.
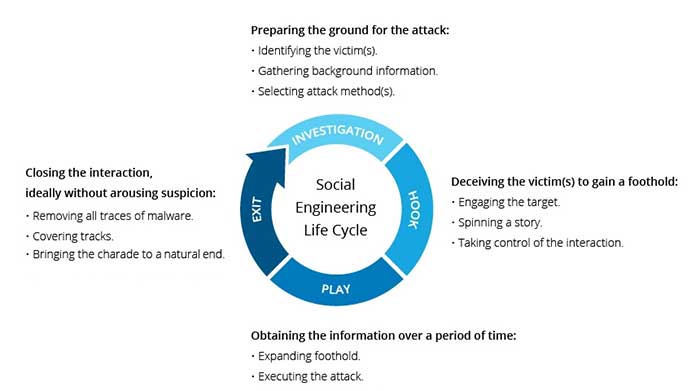
Social engineering attacks occur in one or more steps. An executioner first probes the intended victim to gather necessary background information, such as prospective points of entry and weak security protocols, needed to proceed with the attack.
Then, the attacker moves to gain the victim’s trust and encourages for subsequent actions that break security practices, such as giving away sensitive information or allowing access to critical resources.
It has been found that human error have made social engineering more dangerous rather than weakness of software and operating systems.
Techniques used in attacks
- Baiting attacks use false promise to provoke a sufferer’s greed or curiosity. They attract users into a trap that steals their personal information or strikes their systems with malware.
- Scareware involves victims being bombarded with fake alarms and fictitious threats. Users are misled to think their system is invaded with malware, impelling them to install software that has no real advantage (other than for the perpetrator) or is malware itself.
- Pretexting- Here the attacker generally begins by building trust with their victim by pretending to be co-workers, police, bank and tax officials, or other persons who have right-to-know authority. The pretexter enquires through questions that are superficially required to verify the victim’s identity, through which they put together important personal data.
- Phishing scams are email and text message drives aimed at generating a sense of urgency, curiosity or fear in victims. It then provokes them into unveiling sensitive information, clicking on links to malicious websites, or opening attachments that contain malware.
- Spear Phishing is more intended version of the phishing scam through which an attacker selects specific individuals or enterprises. They then modify their messages based on characteristics, job positions, and contacts belonging to their victims to make their attack less noticeable.
Measures
- Emails and attachments should not be opened from suspicious sources.
- Making use of multifactor authentication can help ensure account protection.
- Be cautious of accepting tempting offers.
- Antivirus/Antimalware should be regularly updated.
Bank of Baroda and several other banks are generating awareness among its customers from falling prey to such attacks. They have shared their authorized toll free numbers. Domestic numbers will start with ‘1’ whereas international ones will start with ‘+91’. Before dialing customers should ensure that the number is starting with ‘1’ and indeed is toll free number. The guidelines also say that banks will NEVER call with these toll free numbers. It was also informed that bank staff will NEVER ask for confidential information like CVV/PIN/ Debit card details, etc. This information should not be shared to anyone as they are only sought by such attackers or fraudsters.